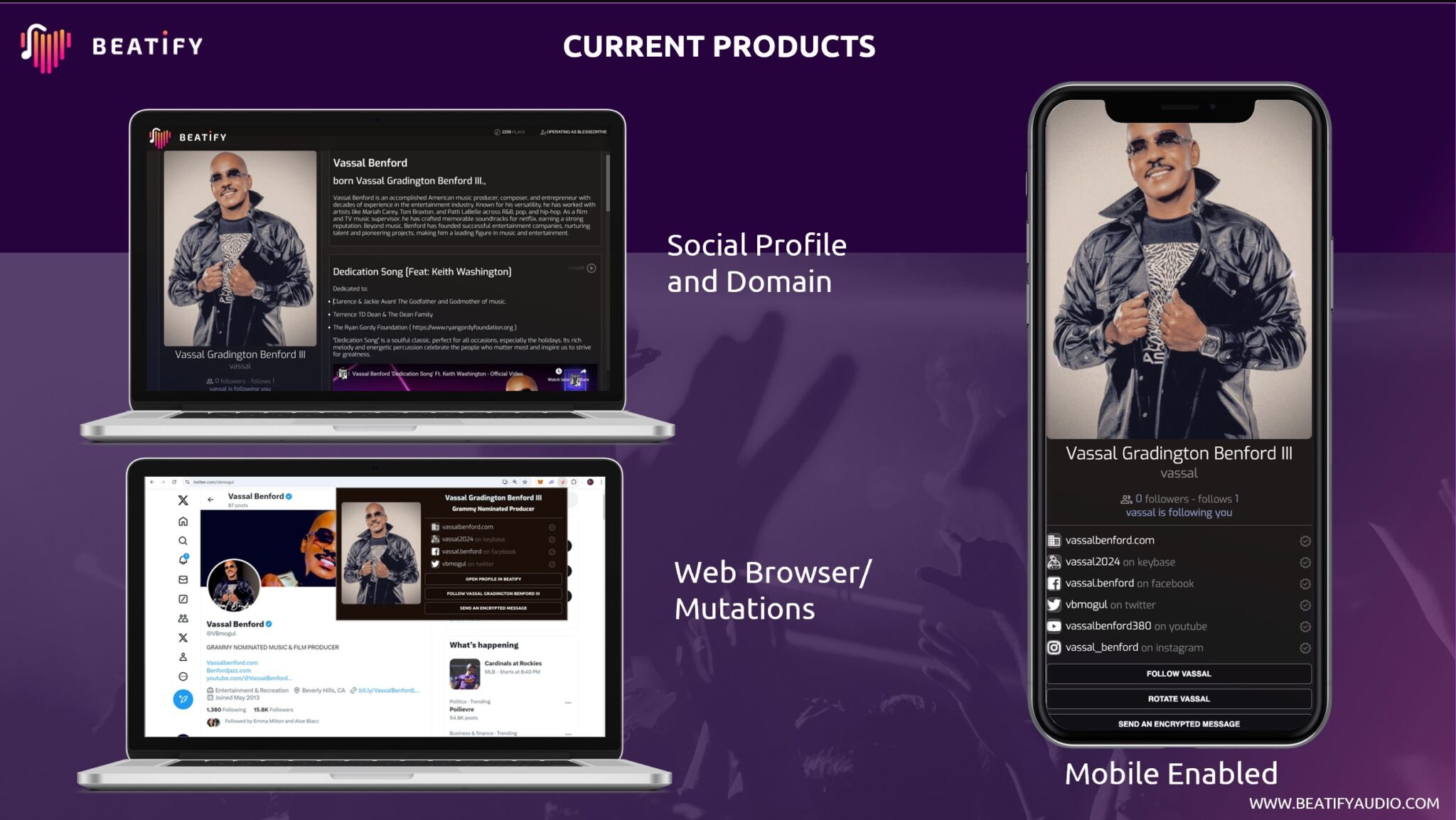
Features
- Sovern Entry
- Sign/Verify
- Proof Builder
- Domain Authenticate
- Pin Content
- Payment Gateway
- Browser Extension
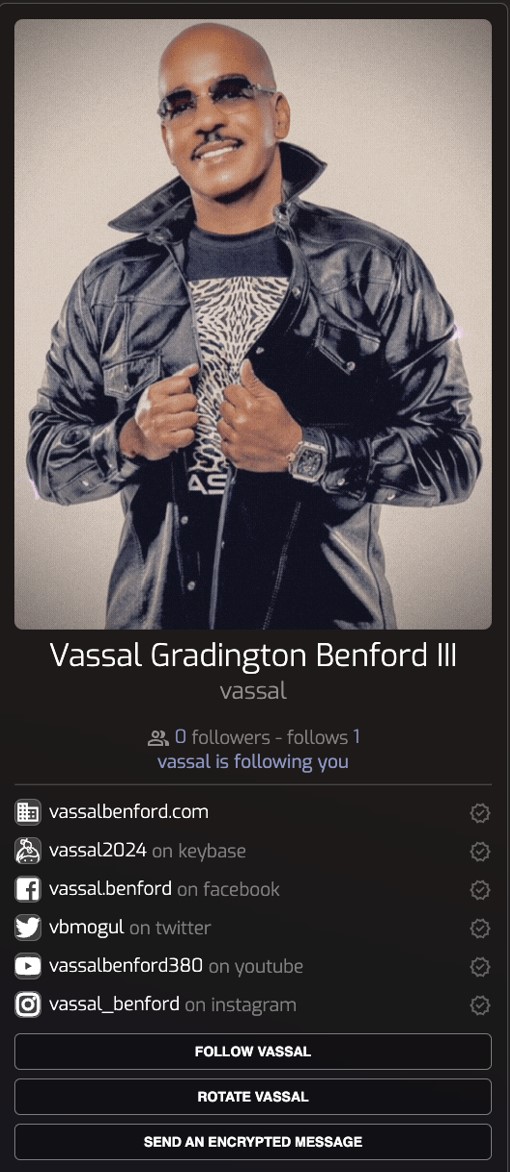
ID Card with Social Proofs
The easy-to-use Proof Builder encourages actors to authenticate themselves
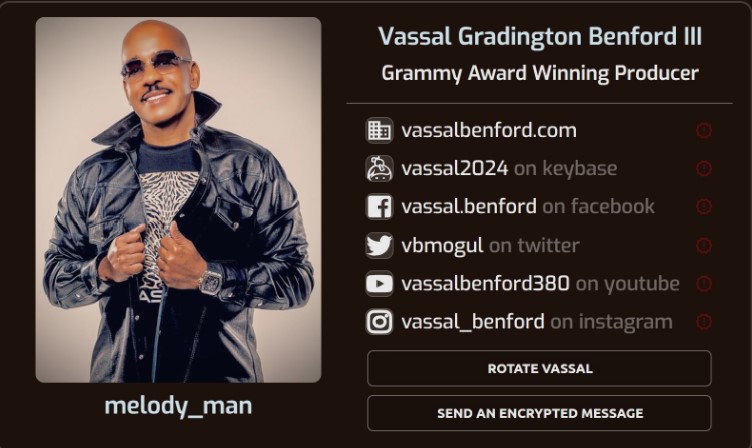
Updated UI/UX Available
Upgrade the UI with our newest model
FAQ
1. What is the white-label digital ID verification service?
This is a fully customizable digital identity verification platform designed to integrate seamlessly into your brand. It includes features like encrypted message verification, identity authentication, and user privacy controls, all tailored to your specific needs.
2. How long does it take to set up the white-label service?
The setup time typically ranges from 2 to 4 weeks, depending on customization requirements and the complexity of integrations with your existing systems.
3. What customization options are available?
You can customize branding (logos, colors, and themes), user interface, onboarding flows, and even specific verification methods to align with your business needs.
4. What industries is this service best suited for?
This service is ideal for industries that require secure identity verification, such as finance, healthcare, education, government services, e-commerce, social platforms, and more.
5. What is included in the turnkey service?
The turnkey package includes:
- Full white-label branding
- Secure user authentication and verification tools
- Integration support for APIs and existing platforms
- Training and documentation for your team
- Ongoing technical support and updates
6. What are the costs associated with using this service?
Costs typically include:
- Setup Fee: One-time fee for initial setup and branding
- Licensing Fee: Monthly fee based on active users or verified identities
- Optional customization fees for advanced features
7. How secure is the platform for identity verification?
The platform uses advanced cryptographic protocols, including PGP encryption and chain-of-trust technology, to ensure secure, tamper-proof verification. It complies with major privacy regulations, such as GDPR and CCPA.
8. Can the platform integrate with my existing system?
Yes, the service provides robust API documentation and support to integrate seamlessly with your existing systems, whether they’re web-based platforms, mobile apps, or other services.
Protect your network now!
You are at risk of malicious actors. Identify actions in your network
© 2022 All Rights Reserved.